In accordance with its purpose to provide “Awaken a world of play in business, with our insights”, Uzabase group aims to continuously develop new products and services that increase the productivity of businesspeople and unleash their creativity.
In order to meet the expectations and trust of customers and society in general, as well as to ensure the safety of crucial information while preserving the convenience and ease of use going forward, We have established a fundamental policy on information security. We intend the fundamental policy as a guideline for our information security initiatives. We will continually improve information security initiatives and prevent recurrence of incidents.
01Continuous development and revision of rules
In addition to complying with various laws and regulations, we will continue to analyze related risks, and create and revise the necessary rules to handle those risks.
02Operation by personnel possessing information-related expertise
We will make continuous efforts to notify employees of any related laws and information security rules, foster information security literacy, and ensure that all executives and regular employees understand the meaning of these laws and regulations and carry out their duties accordingly.
03Utilisation of technology
We will make continuous improvements using various technologies by analyzing the latest technology trends related to information security in order to provide services with enhanced safety while also maintaining their convenience and ease of use.
04Honest attitude and response
In the event of an incident related to information security, we pledge to promptly and accurately disclose any information regarding the incident. We will also investigate the cause of the incident and take steps to prevent recurrence of similar incidents.
Security Management
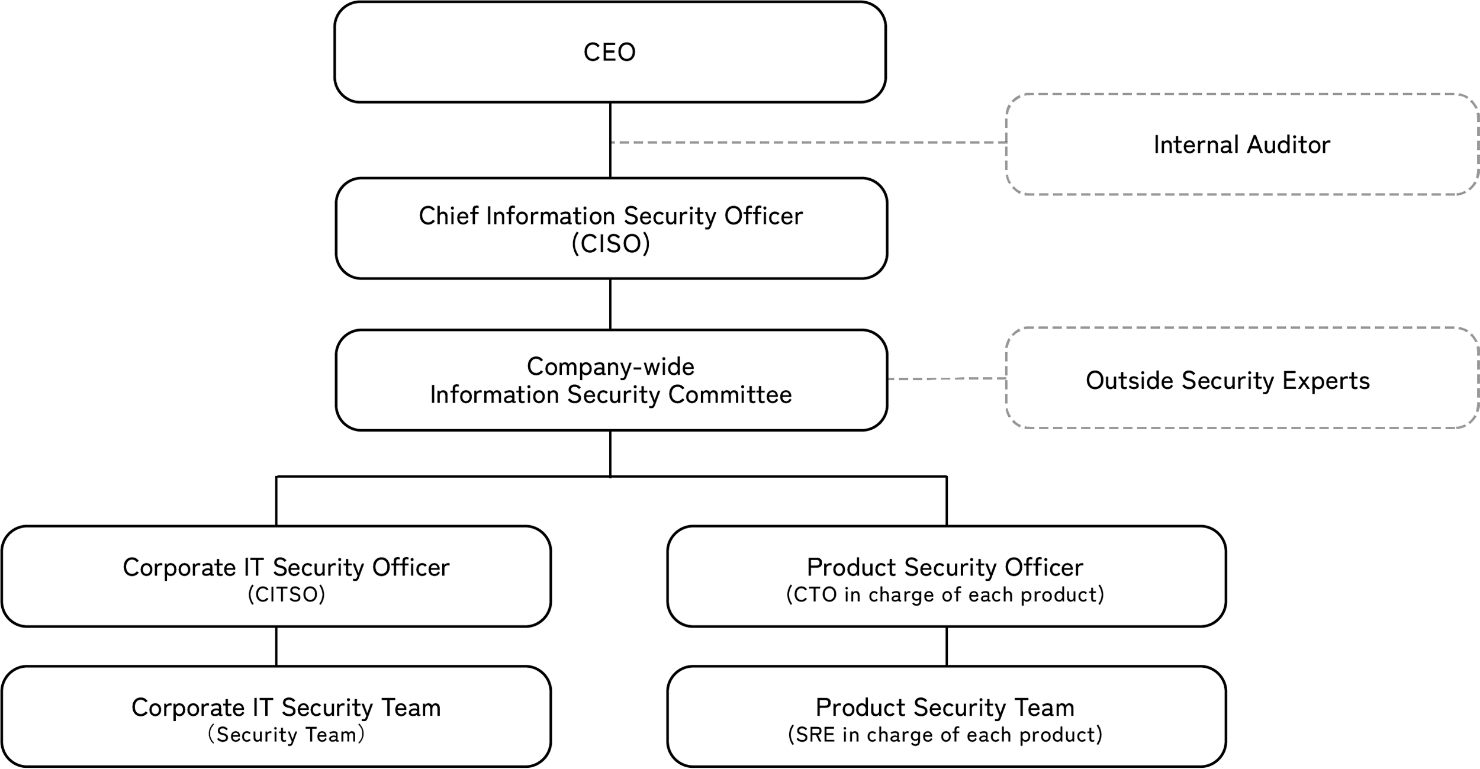
Security References
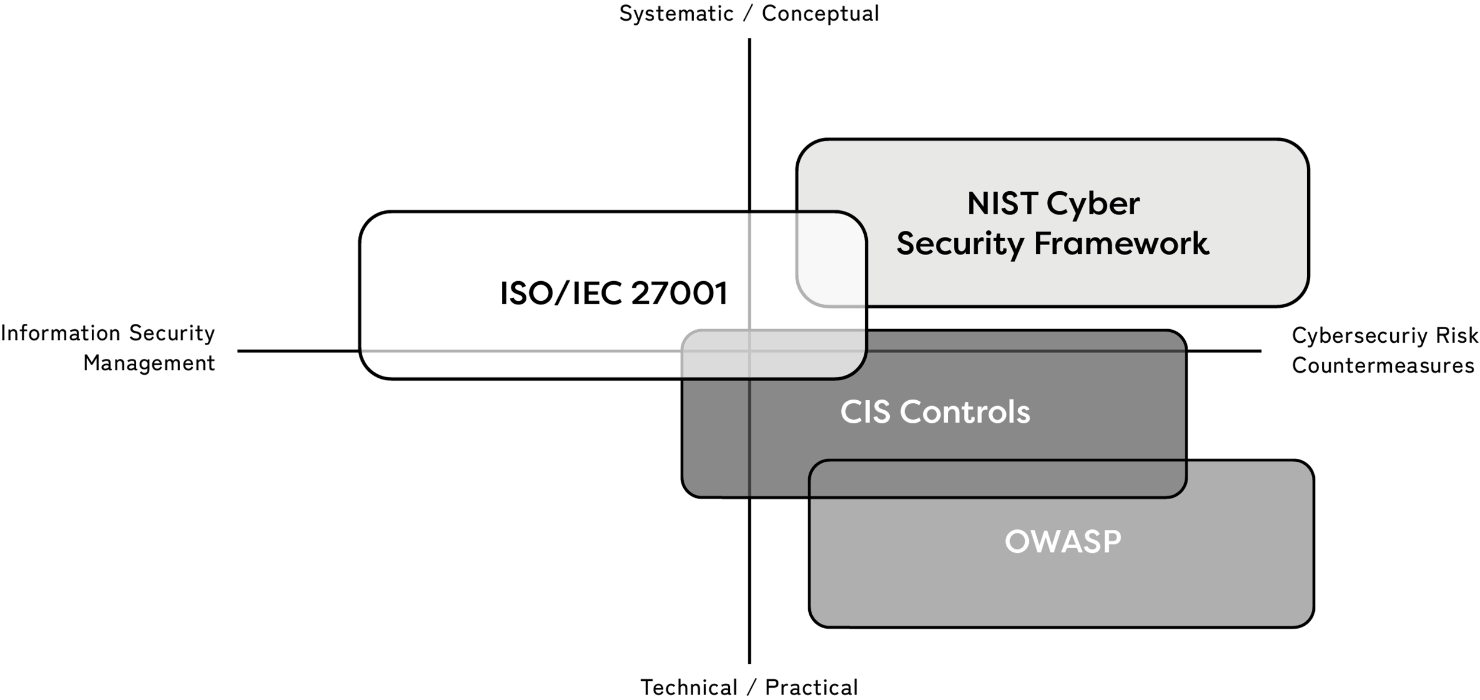
External Certification Body
Regular Security Training
The Uzabase Group conducts regular training sessions on information security designed to improve the security literacy of the entire group, including regular employees, officers, contract workers, part-time employees, interns, and outsourcing partners.
Training Results
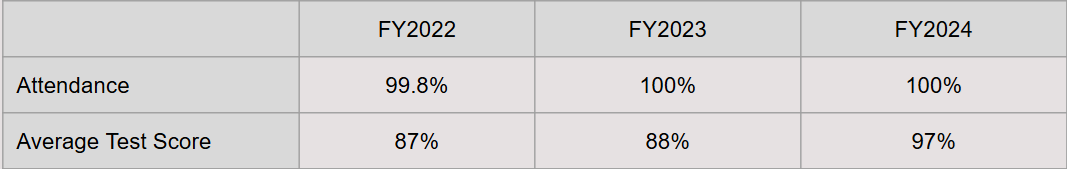
Security Training for New Hires
All new hires undergo security training during which they are introduced to the Uzabase Group’s philosophy on security and the security measures they will be practicing as part of their daily duties.
Corporate IT Security
Secure Authentication & Authorization
Secure system authenticaiton is achieved using multi-factor authentication and single sign-on (SSO) technology. Additionally, systems are linked to personnel information for the purposes of controlling access according to employee roles and responsibilities.
Endpoint Security
Mechanisms are in place to prevent the unauthorized execution of applications, restrict the use of physical media, filter web content, prevent theft, and avoid the leakage of confidential information through unauthorized acquistion of audit logs.
Cyber Resilience
We have introduced a system that constantly monitors endpoints to detect and eliminate suspicious behaviour caused by malware. An operational structure comprising internal resources and external experts is in place to detect threats as quickly as possible and respond to them in such a way as to ensure minimal impact.

Zero Trust Cybersecurity
Other security measures are continuously being implemented using the latest technology to ensure zero-trust cybersecurity.
Product Security

Encryption of Data & Communications
Data is encrypted according to industry-standard encryption methods. Communication routes are encrypted using SSL/TLS to prevent malicious third parties from intercepting, altering, or spoofing the content of communications.

Application Security
Speeding up and stabilizing applications and distributing traffic protects applications from cyber attacks such as SQL injection and DDoS attacks, as well as from data leaks and service failures.

Vulnerability Management
In addition to regular third-party vulnerability assessments, a system has also been implemented for automatically identifying and triaging CVSS and attack code (PoC) for vulnerabilities in OS, middleware, libraries, and other locations to efficiently visualise, manage, and address them.

Secure Development
Other technology-enabled security measures are continuously being worked on, based on the requirements set out in the OWASP(*) framework.
Note(*): US non-profit organisation aiming to improve the security of web applications.
28 April 2023
Uzabase, Inc.
